What is API ?
Application Programming Interface (API) is a software interface that allows two applications to interact with each other without any user intervention. API is a collection of software functions and procedures. In simple terms, API means a software code that can be accessed or executed. API is defined as a code that helps two different software’s to communicate and exchange data with each other.
API offers products or services to communicate with other products and services without having to know how they’re implemented.
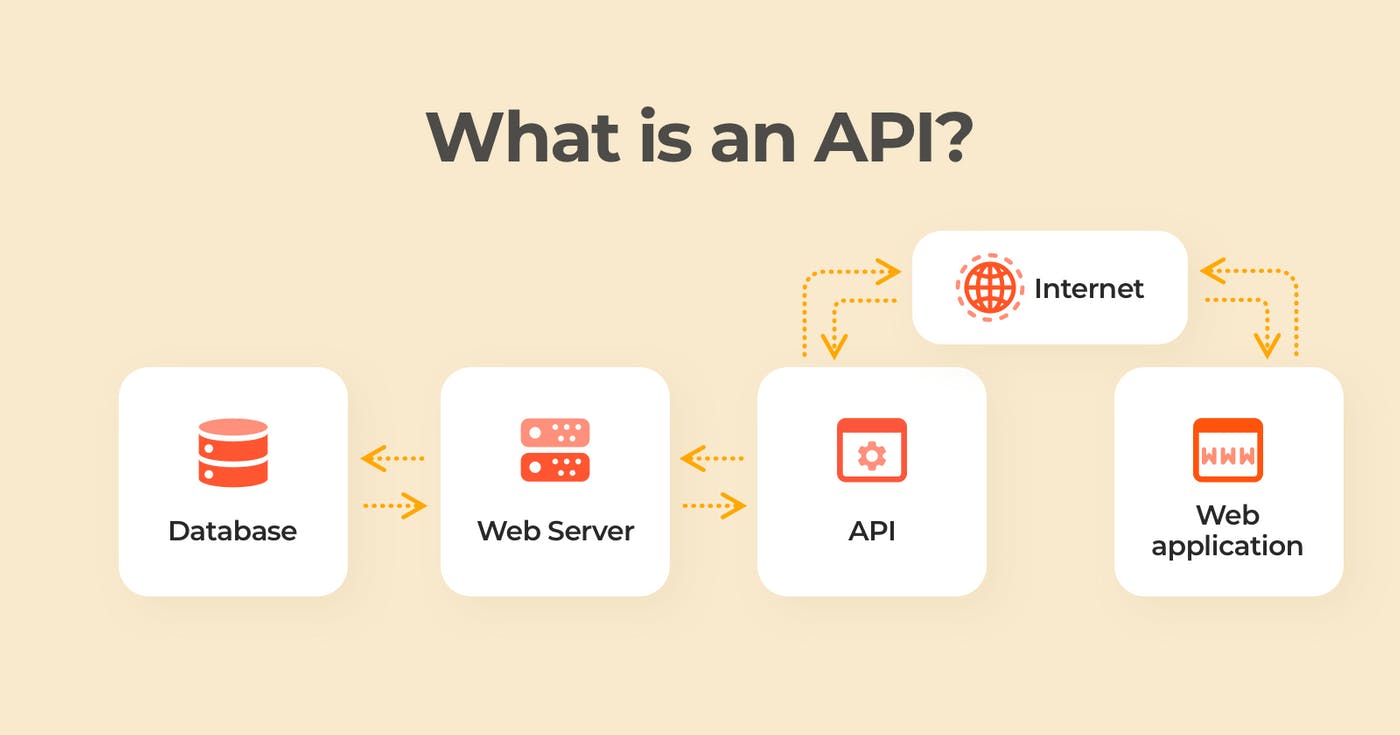
How Does An API Work?
APIs communicate through a set of rules that define how computers, applications or machines can talk to each other. The API acts as a middleman between any two machines that want to connect with each other for a specified task.
An example for better API understanding would be when you sign into Twitter from your phone you are telling the Twitter application that you would like to access your account. The mobile application makes a call to an API to retrieve your Twitter account and credentials. Twitter would then access this information from one of its servers and return the data to the mobile application.
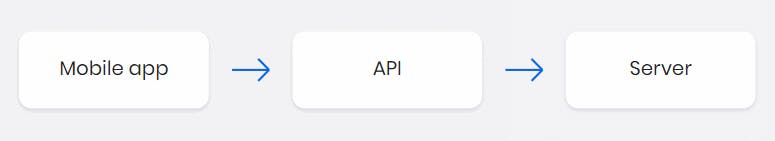
Why do we need an API?
APIs are needed to bring applications together in order to perform a designed function built around sharing data and executing pre-defined processes. They work as the middle man, allowing developers to build new programmatic interactions between the various applications people and businesses use on a daily basis. Generally there are three reasons for using API
APIs Can Help With Your Business Strategy
APIs Assist in Data Management
APIs Promote Business Growth
Types Of API
APIs are broadly accepted and used in web applications. There are four principal types of API commonly used in web-based applications:- public, partner, private and composite.
Open APIs (also called Public APIs) are publicly available for everyone to use.
Partner APIs are custom designed by enterprises to offer access to business partners to reserve or buy specific items, such as tickets or vouchers.
Private (or Internal) APIs are not for public consumption but used for internal processes.
Composite APIs: these combine diverse data and service APIs. They help speed up the course of implementation by essentially bundling multiple API calls together.
What is BLAST ?
BLAST is an open source program and anyone can download and change the program code. This has also given rise to a number of BLAST derivatives. BLAST is highly scalable and comes in a number of different computer platform configuration which makes usage on both small desktop computers and large computer clusters possible.
What is Cherrybomb?
Cherrybomb is a CLI tool that helps you avoid undefined user behavior by validating your API specifications. Our CLI tool is open source, enabling support from both the OpenAPI and Rust communities.
How does Cherrybomb work?
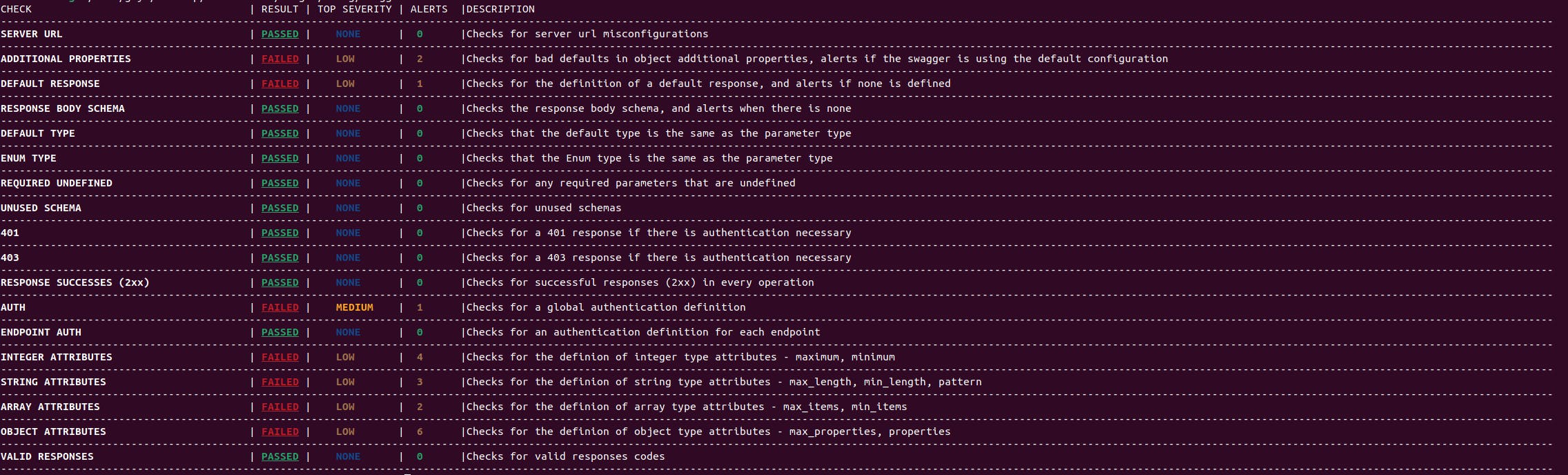
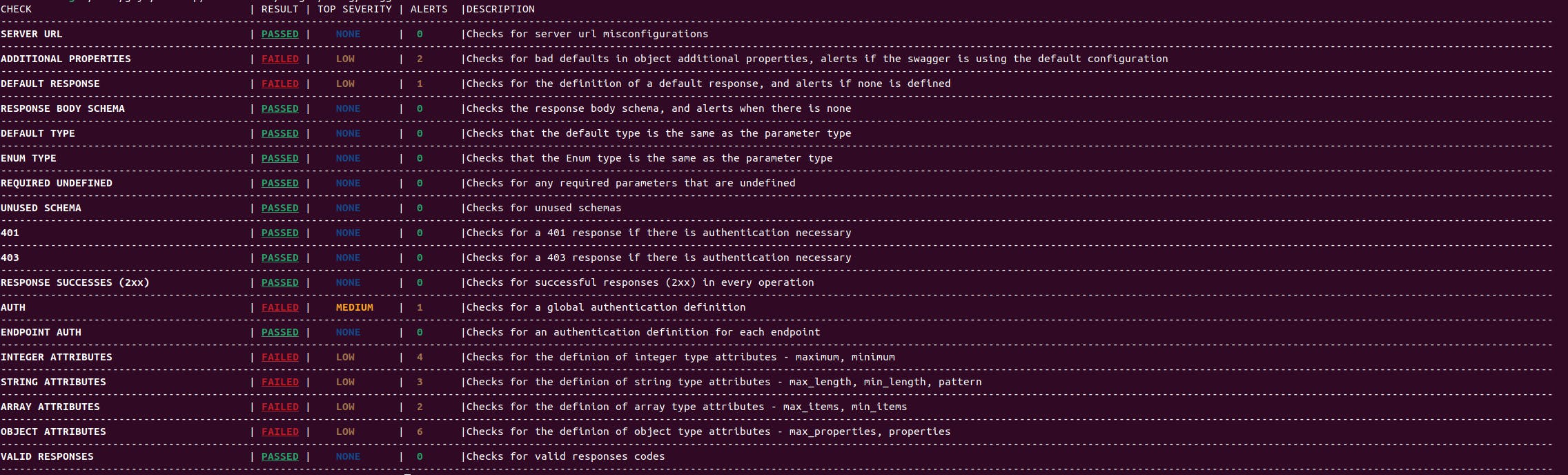
Cherrybomb takes in an OAS file, runs a series of checks on it to make sure everything is on par with the OAS, and outputs a detailed table with any alerts found, guiding you to the exact problem and location to help you solve it quickly.
Features of Cherrybomb
It supports OpenAPI and HTTP Logs.
It can check your logs for business logic flaws.
This makes it easier to use when developing web applications.
The OpenAPI Specification is a standard for specifying how APIs work. The logs can be used to investigate calls.
Installation Of Cherrybomb:-
Using cURL**
Linux/MacOS:
curl https://cherrybomb.blstsecurity.com/install | /bin/bash
The script requires sudo permissions to move the cherrybomb bin into /usr/local/bin/. (If you want to view the shell script(or even help to improving it - https://github.com/blst-security/cherrybomb/blob/main/scripts/install.sh
Direct download
You can also download the binary file directly from https://www.blstsecurity.com/cherrybomb. This is a binary file and you DO NOT have to install Rust. If you use this method you should run this command:
mkdir ~/.cherrybomb
Usage
After installing the CLI, verify it's working by running
cherrybomb --version
OpenAPI specification scan
cherrybomb oas --file <PATH> --config <PATH> --verbosity <0/1/2> --format <cli/txt/json> --output <PATH>
Output example for verbosity level 1:
Output example for verbosity level 0:
Generate Parameter Table
cherrybomb param-table --file <PATH> --name <SINGLE PARAM NAME(OPTIONAL)>
Table output example:
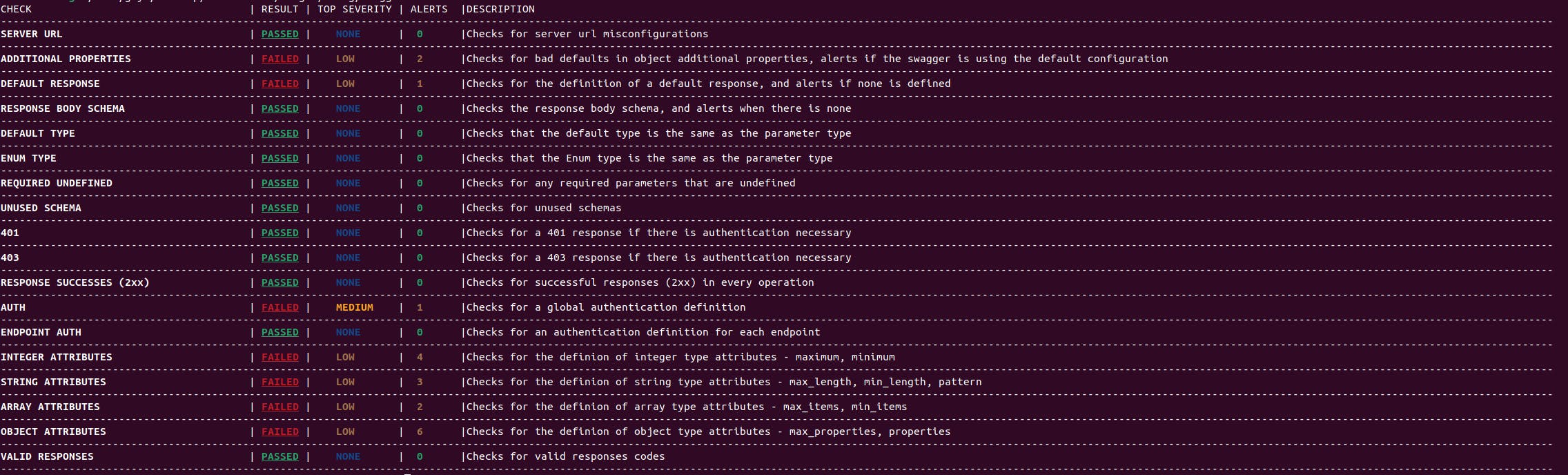
Configuration options: You can configure the OAS scan using the config.json file in your .cherrybomb director that we create by default in your home path(after one scan at least or downloading using the install script).
Go through only part of the checks Full scan:
"scan_type":"Full",
...
}
Only run the server url and the default response checks:
"scan_type":["SERRVER URL","DEFAULT RESPONSE"],
...
}
Fail or not when the highest alert level is info
"fail_on_info":true,
...
}
More Features
First, we have a mapping module that relies on HTTP logs and builds a map of the API. Start mapping your logs by running
cherrybomb map --file <LOGS_FILE_PATH>
--output <OUTPUT_FILE_NAME> --hint <OAS FILE NAME>
In the future, if you want to load new logs to an existing map file, run
cherrybomb load --file <LOGS_FILE_PATH>
--map <MAPPED_FILE_PATH>
Related Links for BLST
Reference
Thank You For Reading My Blog .
Connect with me on Twitter

